-
Fortinet Client For Mac Vpn카테고리 없음 2020. 11. 26. 16:35
- Fortinet Client For Mac
- Forticlient Vpn Client
- Fortinet Vpn Client For Windows
- Fortinet Client For Mac Vpn Setup
In this recipe, you will learn how to create an IPsec VPN on a FortiGate, and connect to it using the default Mac OS X client. This configuration allows Mac users to securely access an internal network and browse the Internet through the VPN tunnel. FortiClient for Mac is a free endpoint protection suite that includes malware/virus detection, rootkit removal, parental web control, and VPN. Malware is detected using updated threat intelligence and definitions from Fortinet's FortiGuard Labs.
▼FortiConverter
Transitioning to next-generation security platforms should be as seamless as possible. FortiConverter makes it easy to migrate complex firewall configurations to Fortinet solutions. FortiConverter’s trial version lets you evaluate the conversion’s accuracy. FortiConverter provides substantial savings in time, costs, and manpower.
Features
Multi-vendor Support - Conversion from Check Point, Cisco, Juniper, Alcatel-Lucent, Palo Alto Networks, and SonicWall. A single tool converts configurations from all supported vendors.FortiOS configuration viewer - Helps FortiGate administrators manually migrate configurations from a FortiGate configuration file by providing a graphical interface to view polices and objects, and copy CLI.Standardized Conversion - Configuration conversion is performed according to conversion rules and policy review and tuning is done after the conversion, prior to generating the output. Human error in the conversion process is minimized.Full Support - A valid FortiConverter license entitles users to direct engineering support and private builds to support their complex conversion projects.FortiExplorer
FortiExplorer is a simple-to-use Fortinet device management application, enabling you to rapidly provision, deploy, and monitor Security Fabric components including FortiGate and FortiWiFi devices from your mobile device. Try it now!
Features
Easily manage configuration & firmware for multiple devicesConfigure and monitor Security Fabric from a mobile device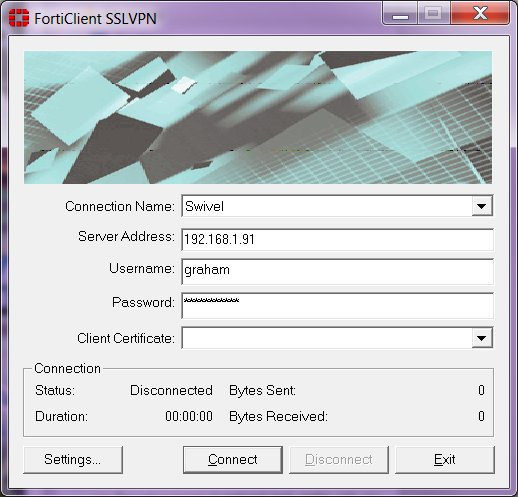
FortiPlanner
FortiPlanner helps you determine the ideal number FortiAP wireless access points (AP) for your premises recommends placement for optimum performance.
This easy-to-use windows application lets you import your building floor plan and draw the walls and other obstructions that can impede with wireless signal. The program then places the right number of APs based on the type of wireless application you choose. The output of the tool is a comprehensive report that can be used to purchase the right number of FAPs as well as maps to aid installation.
The free download can place up to 10 APs. More information and access to the full version can be found via the Fortinet Developer Network. More information on FNDN can be found here.Features
FortiRecorder
FortiCentral is a powerful yet easy-to-use video management system for Windows.
FortiRecorder Mobile iOS and Android Apps user-friendly tools that let you access your FortiRecorder Network Video Recorders (NVRs) from your mobile devices.
Using FortiRecorder Mobile you, or your customers, can view live video from your security cameras, view notifications and play back video events.Features
Features
Features
This section describes how to set up a VPN that is compatible with the Microsoft Windows native VPN, which is Layer 2 Tunneling Protocol (L2TP) with IPsec encryption.
The following topics are included in this section:
Overview
Assumptions
Configuration overview
For troubleshooting information, refer to Troubleshooting L2TP and IPsec.
Overview
The topology of a VPN for Microsoft Windows dialup clients is very similar to the topology for FortiClient Endpoint Security clients.
Example FortiGate VPN configuration with Microsoft clients
Assumptions
For users, the difference is that instead of installing and using the FortiClient application, they configure a network connection using the software built into the Microsoft Windows operating system. Starting in FortiOS 4.0 MR2, you can configure a FortiGate unit to work with unmodified Microsoft VPN client software.
Layer 2 Tunneling Protocol (L2TP)
L2TP is a tunneling protocol published in 1999 that is used with VPNs, as the name suggests. Microsoft Windows operating system has a built-in L2TP client starting since Windows 2000. Mac OS X 10.3 system and higher also have a built-in client.
L2TP provides no encryption and used UDP port 1701. IPsec is used to secure L2TP packets. The initiator of the L2TP tunnel is called the L2TP Access Concentrator (LAC).
L2TP and IPsec is supported for native Windows XP, Windows Vista and Mac OSX native VPN clients. However, in Mac OSX (OSX 10.6.3, including patch releases) the L2TP feature does not work properly on the Mac OS side.
Assumptions
The following assumptions have been made for this example: Sonicwall vpn client for mac.
- L2TP protocol traffic is allowed through network firewalls (TCP and UDP port 1701)
- User has Microsoft Windows 2000 or higher — a Windows version that supports L2TP
Configuration overview
The following section consists of configuring the FortiGate unit and configuring the Windows PC.
Configuring the FortiGate unit
To configure the FortiGate unit, you must:
- Configure LT2P users and firewall user group.
- Configure the L2TP VPN, including the IP address range it assigns to clients.
- Configure an IPsec VPN with encryption and authentication settings that match the Microsoft VPN client.
- Configure security policies.
Configuring LT2P users and firewall user group
Remote users must be authenticated before they can request services and/or access network resources through the VPN. The authentication process can use a password defined on the FortiGate unit or an established external authentication mechanism such as RADIUS or LDAP.
Creating user accounts
You need to create user accounts and then add these users to a firewall user group to be used for L2TP authentication. The Microsoft VPN client can automatically send the user’s Window network logon credentials. You might want to use these for their L2TP user name and password.
Creating a user account – web-based manager
- Go to User & Device > User Definitionand select Create New.
- Enter the User Name.
- Do one of the following:
l Select Password and enter the user’s assigned password.
l Select Match user on LDAP server, Match user on RADIUS server, or Match user onTACACS+
server and select the authentication server from the list. The authentication server must be already configured on the FortiGate unit.
- Select OK.
Creating a user account – CLI
To create a user account called user1 with the password 123_user, enter:
config user local edit user1 set type password set passwd “123_user” set status enable
end
Creating a user group
When clients connect using the L2TP-over-IPsec VPN, the FortiGate unit checks their credentials against the user group you specify for L2TP authentication. You need to create a firewall user group to use for this purpose.
Creating a user group – web-based manager
- Go to User & Device > User Groups, select Create New, and enter the following:
Name Type or edit the user group name (for example, L2TP_group). Type Select Firewall. Available Users/Groups The list of Local users, RADIUS servers, LDAP servers, TACACS+ servers, or PKI users that can be added to the user group. To add a member to this list, select the name and then select the right arrow button. Members The list of Local users, RADIUS servers, LDAP servers, TACACS+ servers, or PKI users that belong to the user group. To remove a member, select the name and then select the left arrow button. - Select OK.
Creating a user group – CLI
To create the user group L2TP_group and add members User_1, User_2, and User_3, enter:
config user group edit L2TP_group set group-type firewall set member User_1 User_2 User_3 end
Configuring L2TP
You can only configure L2TP settings in the CLI. As well as enabling L2TP, you set the range of IP address values that are assigned to L2TP clients and specify the user group that can access the VPN. For example, to allow access to users in the L2TP_group and assign them addresses in the range 192.168.0.50 to 192.168.0.59, enter:
config vpn l2tp set sip 192.168.0.50 set eip 192.168.0.59 set status enable set usrgrp “L2TP_group”
end
One of the security policies for the L2TP over IPsec VPN uses the client address range, so you need also need to create a firewall address for that range. For example,
config firewall address edit L2TPclients set type iprange set start-ip 192.168.0.50 set end-ip 192.168.0.59
end
Alternatively, you could define this range in the web-based manager.
Configuring IPsec
The Microsoft VPN client uses IPsec for encryption. The configuration needed on the FortiGate unit is the same as for any other IPsec VPN with the following exceptions.
- Transport mode is used instead of tunnel mode.
- The encryption and authentication proposals must be compatible with the Microsoft client.
L2TP over IPsec is supported on the FortiGate unit for both policy-based and route-based configurations, but the following example is policy-based.
Configuring Phase 1 – web-based manager
- Go to VPN > IPsec Tunnels and create the new custom tunnel or edit an existing tunnel.
- Edit the Phase 1 Proposal (if it is not available, you may need to click the Convert to Custom Tunnel button).
Name Enter a name for this VPN, dialup_p1 for example. Remote Gateway Dialup User Local Interface Select the network interface that connects to the Internet. For example, port1. Mode Main (ID protection) Authentication Method Preshared Key Pre-shared Key Enter the preshared key. This key must also be entered in the Microsoft VPN client. Advanced Select Advanced to enter the following information. Phase 1 Proposal Enter the following Encryption/Authentication pairs: AES256-MD5, 3DES-SHA1, AES192-SHA1
Diffie-Hellman Group 2 NAT Traversal Enable Dead Peer Detection Enable Configuring Phase 1 – CLI
To create a Phase 1 configuration called dialup_p1 on a FortiGate unit that has port1 connected to the Internet, you would enter: Is there a naruto online mini client for mac.

config vpn ipsec phase1 edit dialup_p1 set type dynamic set interface port1 set mode main set psksecret ********
set proposal aes256-md5 3des-sha1 aes192-sha1 set dhgrp 2 set nattraversal enable
set dpd [disable | on-idle | on-demand]
end
It is worth noting here that the command config vpn ipsec phase1 is used rather than config vpn ipsec phase1-interface because this configuration is policy-based and not route-based.
Configuring Phase 2 – web-based manager
- Open the Phase 2 Selectors
- Enter the following information and then select OK.
Phase 2 Proposal Enter the following Encryption/Authentication pairs: AES256-MD5, 3DES-SHA1, AES192-SHA1
Enable replay detection Enable Enable perfect forward secrecy (PFS) Disable Keylife 3600 seconds - Make this a transport-mode VPN. You must use the CLI to do this. If your Phase 2 name is dialup_p2, you would enter:
config vpn ipsec phase2 edit dialup_p2 set encapsulation transport-mode
end
Configuring Phase 2 – CLI
Fortinet Client For Mac
To configure a Phase 2 to work with your phase_1 configuration, you would enter:
config vpn ipsec phase2 edit dialup_p2 set phase1name dialup_p1
set proposal aes256-md5 3des-sha1 aes192-sha1 set replay enable set pfs disable set keylifeseconds 3600 set encapsulation transport-mode
end
Once again, note here that the command config vpn ipsec phase2 is used rather than config vpn ipsec phase2-interface because this configuration is policy-based and not route-based.
Forticlient Vpn Client
Configuring security policies
The security policies required for L2TP over IPsec VPN are:
- An IPsec policy, as you would create for any policy-based IPsec VPN
- A regular ACCEPT policy to allow traffic from the L2TP clients to access the protected network
Configuring the IPsec security policy – web-based manager
- Go to System > Feature Visibility and enable Policy-based IPsec VPN.
- Go to Policy & Objects > IPv4 Policy and select Create New.
- Set the Action to IPsec and enter the following information:
Incoming Interface Select the interface that connects to the private network behind this FortiGate unit. Source Address All Outgoing Interface Select the FortiGate unit’s public interface. Destination Address All VPN Tunnel Select Use Existing and select the name of the Phase 1 configuration that you created. For example, dialup_p1. See Configuring IPsec on page 182. Allow traffic to be initiated from the remote site enable - Select OK.
Configuring the IPsec security policy – CLI
If your VPN tunnel (Phase 1) is called dialup_p1, your protected network is on port2, and your public interface is port1, you would enter:
config firewall policy edit 0 set srcintf port2 set dstintf port1 set srcaddr all set dstaddr all set action ipsec set schedule always set service all set inbound enable set vpntunnel dialup_p1
end
Configuring the ACCEPT security policy – web-based manager
- Go to Policy & Objects > IPv4 Policy and select Create New.
- Leave the Policy Type as Firewall and leave the Policy Subtype as Address.
- Enter the following information and select OK:
Incoming Interface Select the FortiGate unit’s public interface. Source Address Select the firewall address that you defined for the L2TP clients. Outgoing Interface Select the interface that connects to the private network behind this FortiGate unit. Destination Address All Action ACCEPT Configuring the ACCEPT security policy – CLI
If your public interface is port1, your protected network is on port2, and L2TPclients is the address range that L2TP clients use, you would enter: config firewall policy
edit 1 set srcintf port1 set dstintf port2 set srcaddr L2TPclients set dstaddr all set action accept set schedule always set service all
end
Configuring the Windows PC
Configuration of the Windows PC for a VPN connection to the FortiGate unit consists of the following:
- In Network Connections, configure a Virtual Private Network connection to the FortiGate unit.
- Ensure that the IPSEC service is running.
- Ensure that IPsec has not been disabled for the VPN client. It may have been disabled to make the Microsoft VPN compatible with an earlier version of FortiOS.
The instructions in this section are based on Windows XP. Other versions of Windows may vary slightly.
Configuring the network connection
- Open Network Connections.
This is available through the Control Panel.
- Double-click New Connection Wizard and Select Next.
- Select Connect to the network at my workplace.
- Select Next.
- Select Virtual Private Network connection and select Next.
- In the Company Name field, enter a name for the connection and select Next.
- Select Do not dial the initial connection and then select Next.
- Enter the public IP address or FQDN of the FortiGate unit and select Next.
- Optionally, select Add a shortcut to this connection to my desktop.
- Select Finish.
The Connect dialog opens on the desktop.
- Select Properties and then select the Security
- Select IPsec Settings.
- Select Use pre-shared key for authentication, enter the preshared key that you configured for your VPN, and select OK. Select OK.
Checking that the IPsec service is running
- Open Administrative Tools through the Control Panel.
- Double-click Services.
- Look for IPSEC Services. Confirm that the Startup Type is Automatic and Status is set to Started. If needed, double-click IPsec Services to change these settings.
Checking that IPsec has not been disabled
- Select Start > Run.
- Enter regedit and select OK.
- Find the Registry key HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesRasManParameters
- If there is a ProhibitIPsec value, it must be set to 0.
Fortinet Vpn Client For Windows
Enforcing IPsec in L2TP configuration
An enforce-ipsec option is available in L2TP configuration to force the FortiGate L2TP server to accept only IPsec encrypted connections.
Syntax
config vpn l2tp set eip 50.0.0.100 set sip 50.0.0.1 set status enable
set enforce-ipsec-interface {disable | enable} (default = disable) set usrgrp <group_name> end
Having trouble configuring your Fortinet hardware or have some questions you need answered? Ask your questions in the comments below!!! Want someone else to deal with it for you? Get some consulting from Fortinet GURU!Fortinet Client For Mac Vpn Setup
Don't Forget To Buy Your Fortinet Hardware From The Fortinet GURU